Summary
Password, key, or identification is the most broadly used and is one of the most important tools used by organizations to authenticate applications and users, providing them with sensitive systems, information, and services. Because secrets have to be transmitted securely, secret management has to account for and mitigate the risks to these secrets both in transit and at rest.
Goals
In this tutorial, we will create a simple lambda function, We will also be creating a registration form screen, login screen using AWS cognito and an api gateway from AWS. This application will contain vital information like a JWT token we would like to keep safe and secure, so we can learn how to manage that token with Doppler
Why Secret Management
Tokens, passwords, and keys are the most broadly used form of authentication for authenticating users and other applications before they can access any other service on your application or collect any sensitive information that they would need. Notwithstanding, hackers are on the loose looking for systems that they can exploit from time to time, and to help save yourself or the organization you work for, some money, all secrets that concern your application must be securely stored.
Doppler as a Secret Management Solution
Passwords and other secrets are needed to authenticate Application to Application(A2A) and Authentication to Database(A2B) communication and access. Most at times, applications and IoT devices are shipped and deployed with hardcoded credentials which are easily crackable by hackers with a simple dictionary method attack but with Doppler, you don’t have to keep those keys in those scripts anymore as you can securely keep them in Doppler. Doppler has improved my productivity in just a little time of using the platform. Doppler provides its users with easy ways to set up projects as their documentation is easy and simple to understand.
Let's dive right into this tutorial and see how Doppler can make things so easy.
Create users using AWS Cognito
We are going to create users on AWS cognito which has a hosted UI which users can use to sign up and sign in users and it is a very simple work through if you follow the instructions. Below is an image of the user I created.
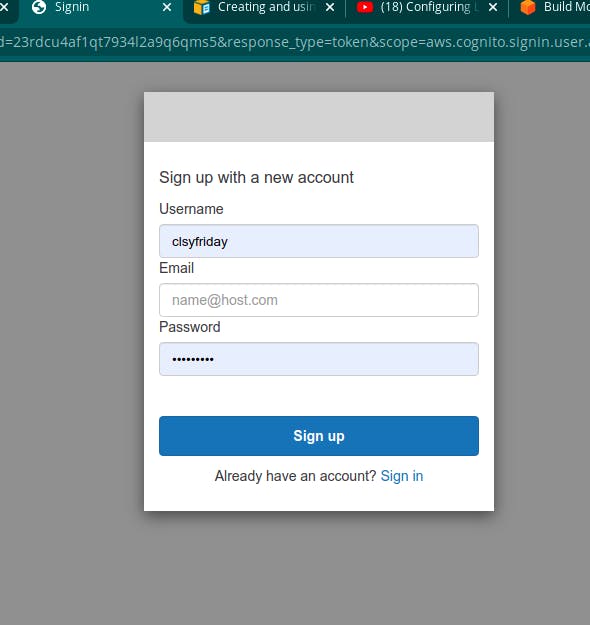
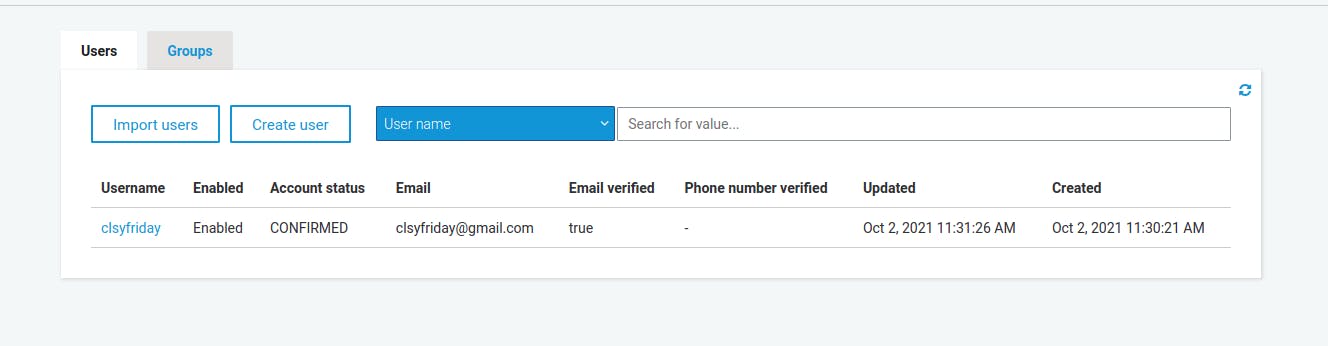
Our aim of creating this user is to make sure only authenticated users can login to use our app services and we will achieve this using an AWS gate-way that will give us a JWT token, specific to every user and it is this token we will want to secure because we would not want that token to be displayed on the frontend because it can be accessed by anybody and be used to cause severe havoc to our app.
Create a lambda function
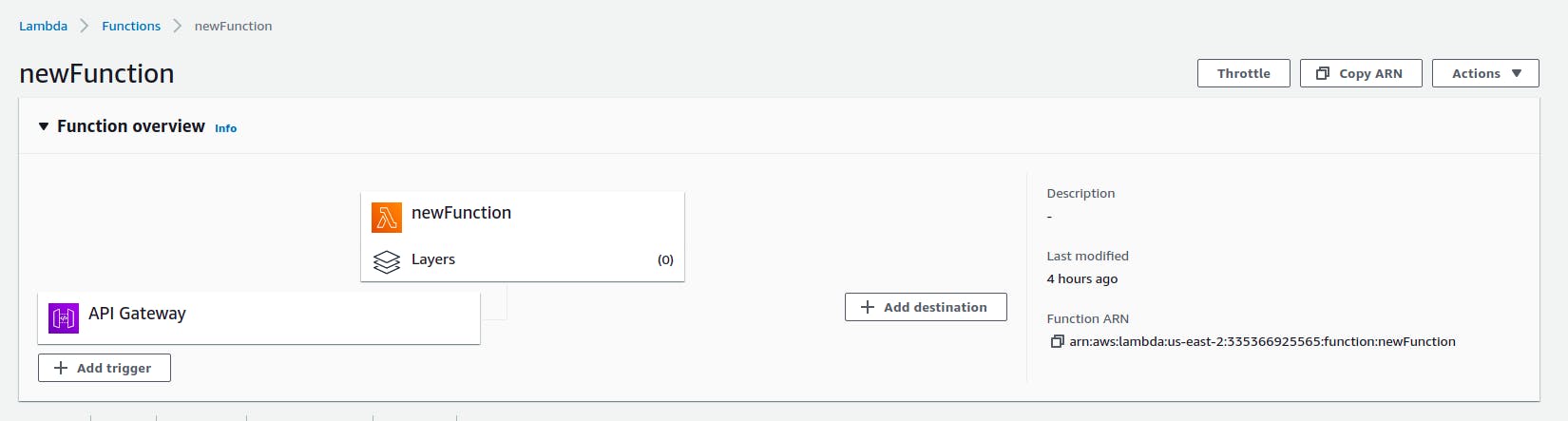
So let’s create a lambda function that will use an api gate-way that will help us get a JWT token to authenticate our users. We won’t be getting much detail on creating a lambda function or adding the api gateway as our main focus is to add our JWT token to Doppler. Below is an image of the lambda function we have created which we will integrate with the api gateway a little later.
Add API Gateway
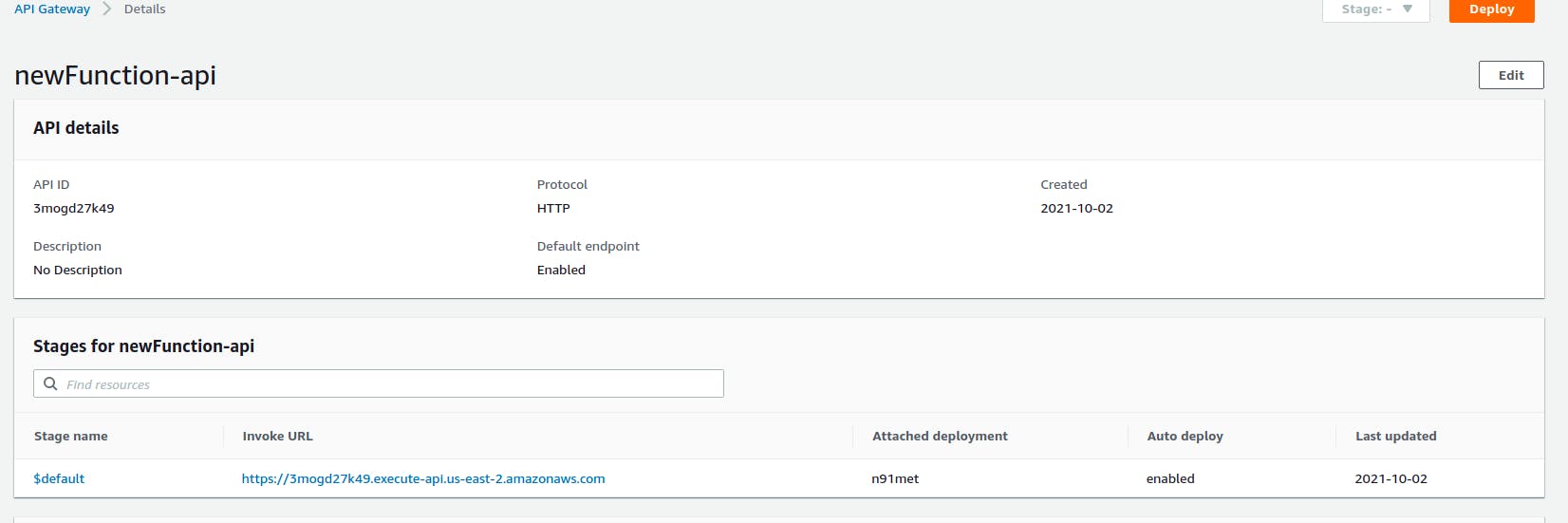
Amazon API Gateway is an AWS service for creating and securing REST, HTTP, and WebSocket APIs at any scale. API developers can create APIs that access AWS or other web services, as well as data stored in the AWS Cloud. We will be creating a HTTP gateway in this case.
Create a project on Doppler
Creating a project on Doppler is extremely simple and straightforward, all you just need to do is to hit the plus icon to create a new project. Log on to your Doppler account and create a new project sort of like so
Once a new project is created, three stages/environments are created which are
Development
Staging
Production
These environments are where we store our secrets.
Sync Doppler with AWS Secret Manager
Before we can sync our secrets with Doppler, we will need to integrate AWS secret manager with Doppler and sync AWS with Doppler, let us follow the steps below
After creating a project, click on integrations
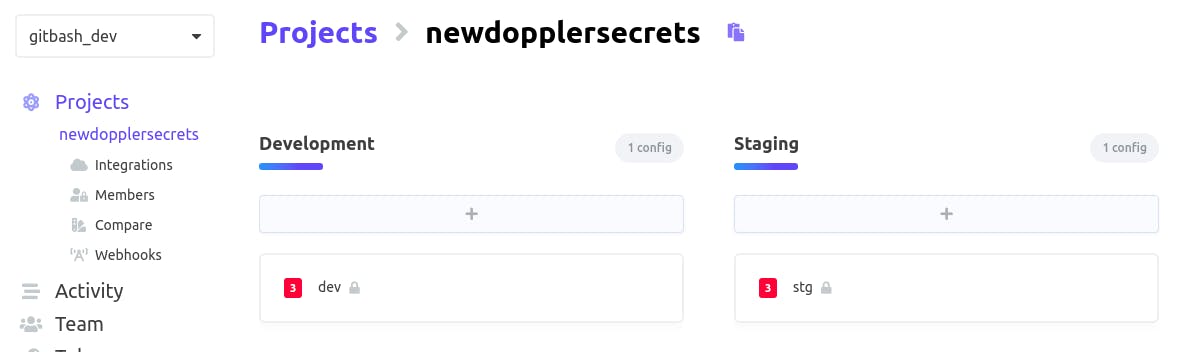
When you click on integrations, it should take us to a new web page where we will see a list of different services we can integrate Doppler with but in our case, we will be using Secrets Manager for integration.

Click on Secrets Manager and we will be directed to another page where we will be asked to give the key ID and Access key to our AWS secrets manager. If you do not have one, you can get it while creating a new AWS Amplify user after hitting the Create User button, but if you have one, this is how you access it
Go to I AM management console > select users > Select the current user
You should see something like this
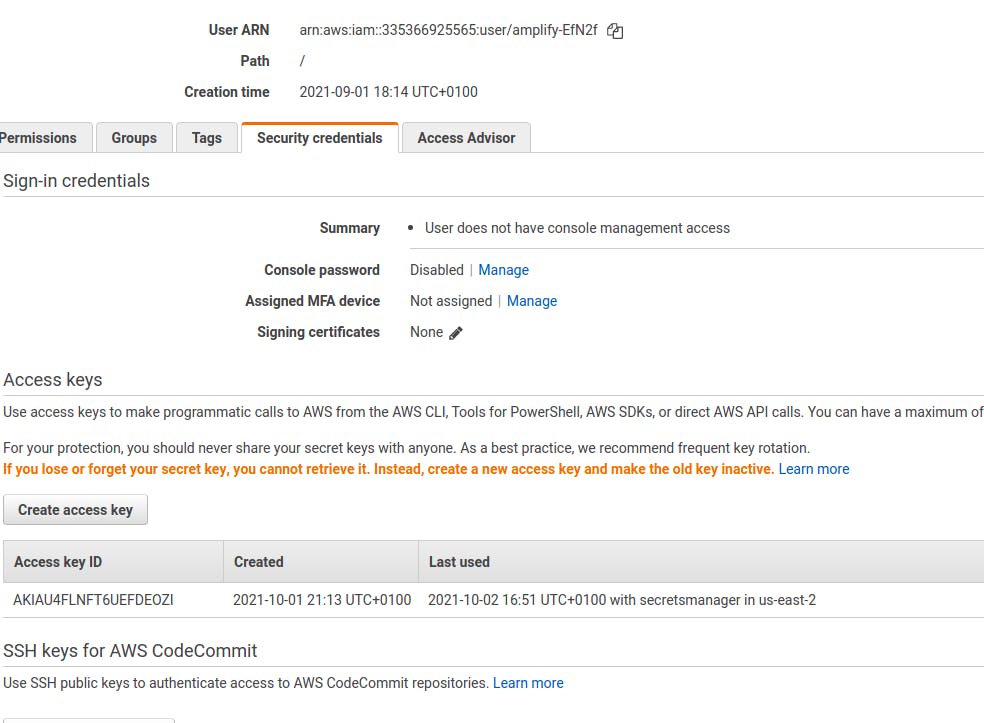
This is where you will find your Access Key ID and then you will have to generate a new Access key. Add these keys above to Doppler to sync with your AWS secret manager.

Doppler requires permissions to integrate with our AWS secret manager and these policies can easily be added in JSON format.
If you have an already existing IAM user and you want to add a new policy, it is pretty easy. Search for the keyword IAM in the AWS search box and it will show you the IAM AWS feature, click on it, and next select Users. The first open tab is the permissions tab
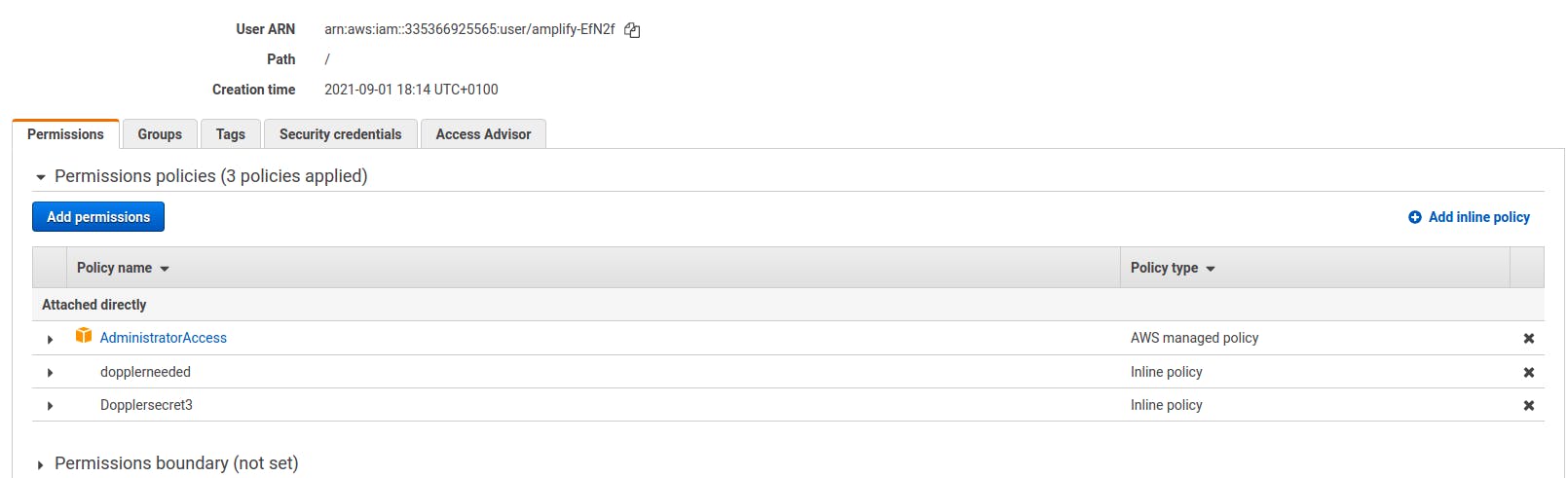
Click on Add Inline Policy to create a custom policy, give it a name and add these policies in JSON format
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowSecretsManagerAccess",
"Effect": "Allow",
"Action": [
"secretsmanager:GetSecretValue",
"secretsmanager:DescribeSecret",
"secretsmanager:PutSecretValue",
"secretsmanager:CreateSecret",
"secretsmanager:DeleteSecret",
"secretsmanager:TagResource",
"secretsmanager:UpdateSecret"
],
"Resource": "*"
}
]
}
Furthermore, after adding our Keys to integrate Doppler with AWS secret manager, we need to configure the Doppler environment.

Select config to sync, the AWS Region where mine is US-east-2 and optionally choose a path in Doppler where all your secrets from AWS will be stored.
Save JWT token to Doppler
To get our JWT token, after the user signs in, look on your browser search bar, we will copy that token and store it on Doppler as so
And now the most interesting part of this topic is to store this secret token on Doppler.
After syncing your new project to AWS, open the newly created project on your Doppler dashboard.
newdopplersecrets
Choose the new project that you created and synced with AWS, I will be choosing
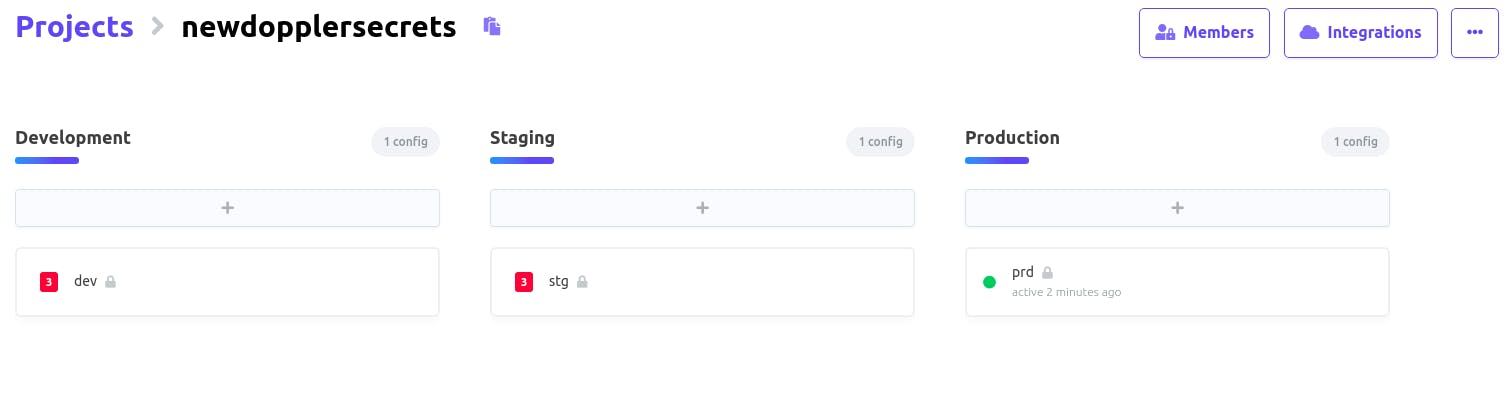
Recall that you chose an environment while syncing to AWS and in my case, I chose
Production(prd)
That is why according to the image above, prd is colored green because it is active.
We will click on the active environment to navigate to a new page where we can add the secrets we want to upload on AWS.
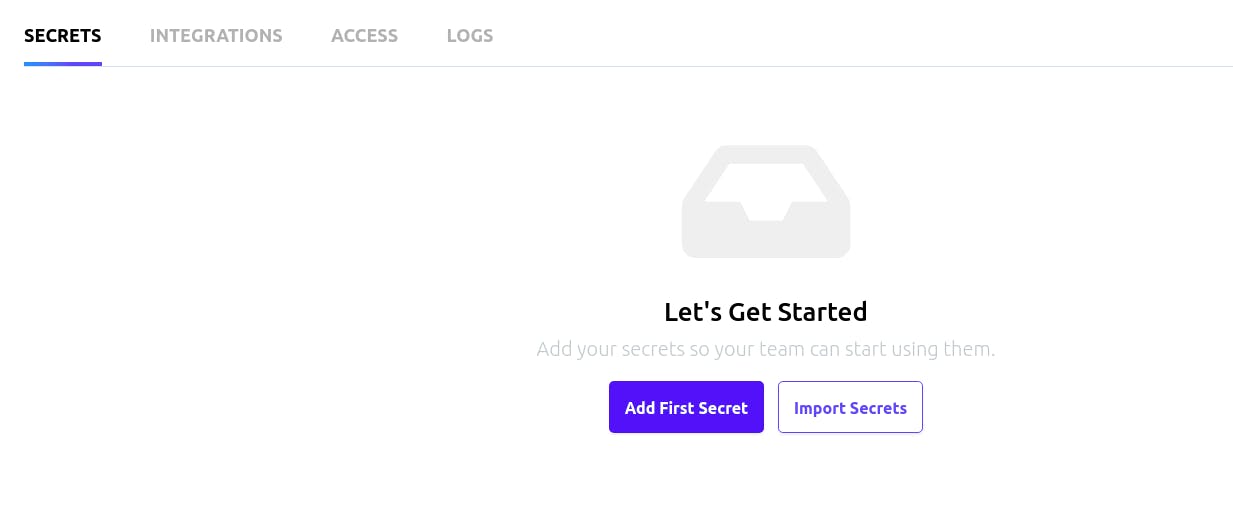
The image above should be the next page we will see, click on the Add First Secret button to add the JWT token we copied from the browser earlier. You can add any key name and the token as value
BASE_URL : https://doppler.com
BEARER_TOKEN : eyJraWQiOiJCUVRvNG9pSHNoK3FodGUrNGwydW9JKzBXZjFsK2tMQkJpckw3dHlXeUFNPSIsImFsZyI6IlJTMjU2In0.eyJhdF9oYXNoIjoiN19fa3VxOG5nV1hiN3ZEZmNTSTJaUSIsInN1YiI6ImU3YjQ0YWRjLTkyYjUtNDZmOS04M2EzLTlkNGMyMDc1ZmM0NiIsImVtYWlsX3ZlcmlmaWVkIjp0cnVlLCJpc3MiOiJodHRwczpcL1wvY29nbml0by1pZHAudXMtZWFzdC0yLmFtYXpvbmF3cy5jb21cL3VzLWVhc3QtMl9KM2ppVmtrbGIiLCJjb2duaXRvOnVzZXJuYW1lIjoiY2xzeWZyaWRheSIsImF1ZCI6IjIzcmRjdTRhZjFxdDc5MzRsMmE5cTZxbXM1IiwiZXZlbnRfaWQiOiJjNzdkZjdjZS1hZGE1LTQ4YmYtODM2YS0yNzJmYjViMmJkYjkiLCJ0b2tlbl91c2UiOiJpZCIsImF1dGhfdGltZSI6MTYzMzE3NDI4NiwiZXhwIjoxNjMzMTc3ODg2LCJpYXQiOjE2MzMxNzQyODYsImp0aSI6IjY5NjhiZjZkLWEwYzAtNDkyZi04ODA0LWQ0ZjE2OTRkMWY4YiIsImVtYWlsIjoiY2xzeWZyaWRheUBnbWFpbC5jb20ifQ.U43PFIzcIJOk0MHmCr1a87WKXE4LIosl7ZvoO6Eo27d_rnxGHeUyrP4r0xH9XUeAH7zQR6e4Uk75hCNI1RgD0wpgbaOrmVfnZGnnrBBJTVN9BKs2ZrcPd_53ky8vwSNKAaTYlqvCNRnzARZim85HCYdL0aJaqz-R0jteyb0_7aEvaum2RMHG6RYJ0aYP46fNv8TaYW9imlvGs774kKzLmnHuIHwfN74iHxs68tcT0HcTHMUWqlo08uIZ3szceLszRqmSc7DjU24-Y1qvcsMh01eHbUDq-pdmZTUqaQ1uVTY1vBs-EhlrYNKOr8P-oBga6CiwXWXTfPmf_BYM2pTtvw
PASSWORD : 0123456789
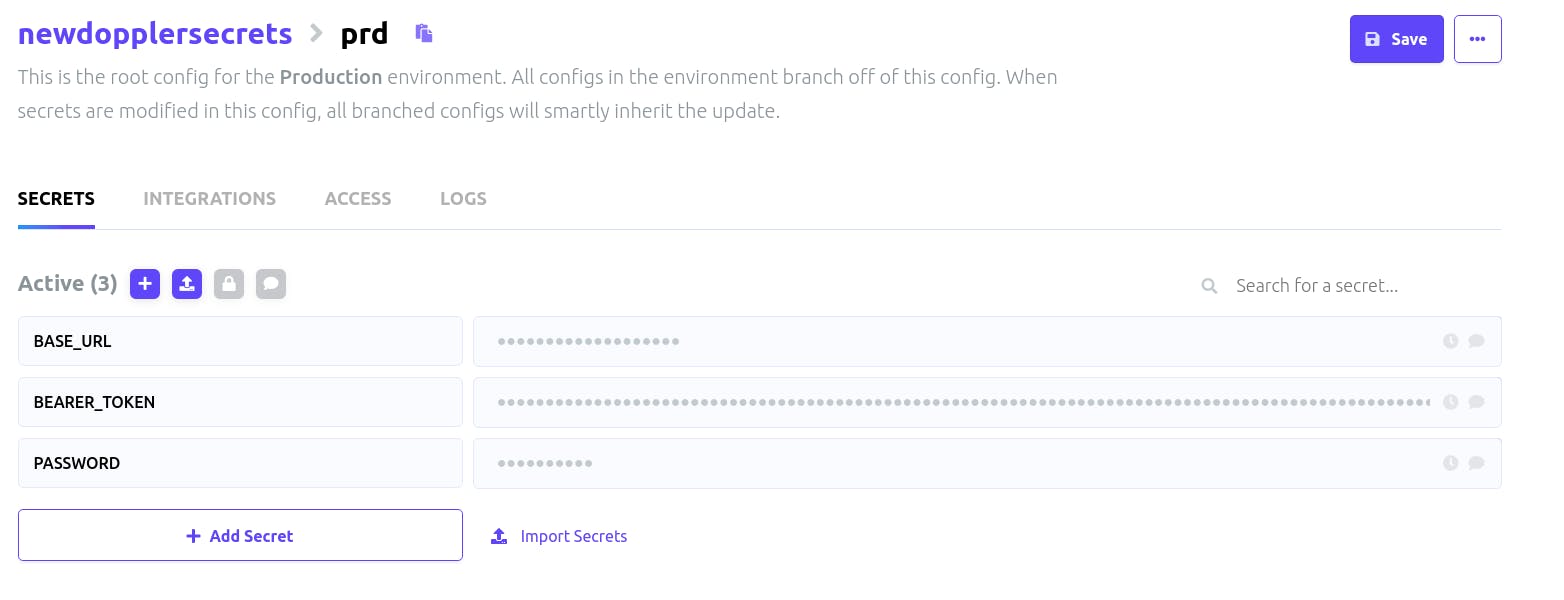
After adding keys and values, your secrets should look like the image above, we should hit the save button at the top right to save our secrets.
Furthermore, click on the next tab titled Integrations and we should see this
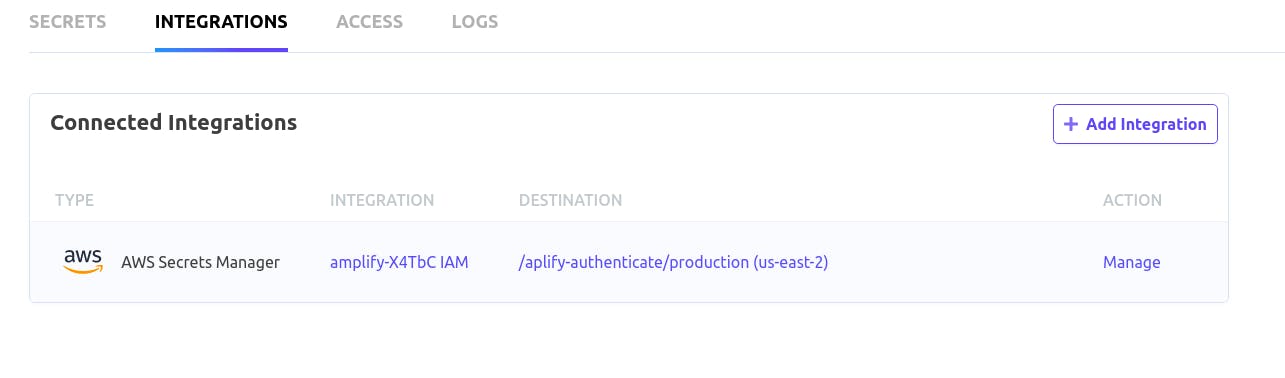
Now let us click on the text Manage at the extreme, it should lead us to a new web page where we can hit sync to upload all our secrets to AWS secret manager.
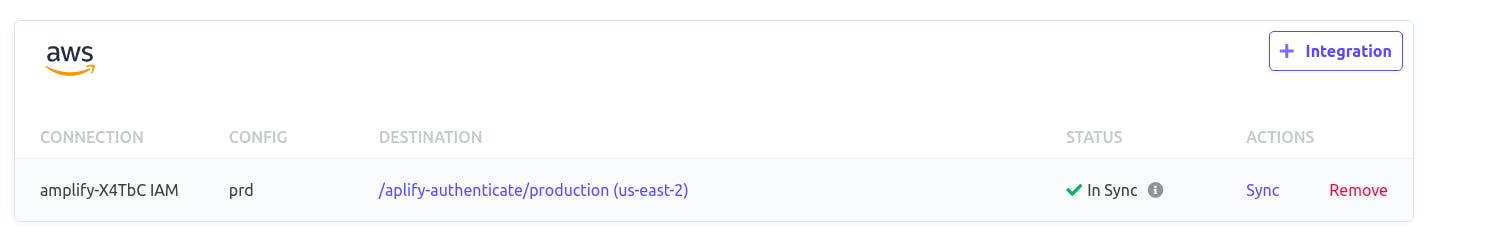
Hit the Sync text and all our secrets will be added to AWS Secrets manager. To confirm that all our secrets got uploaded to AWS from Doppler, click the link under the DESTINATION tab just like the picture above and we should see the name doppler added to the project name we created in AWS.
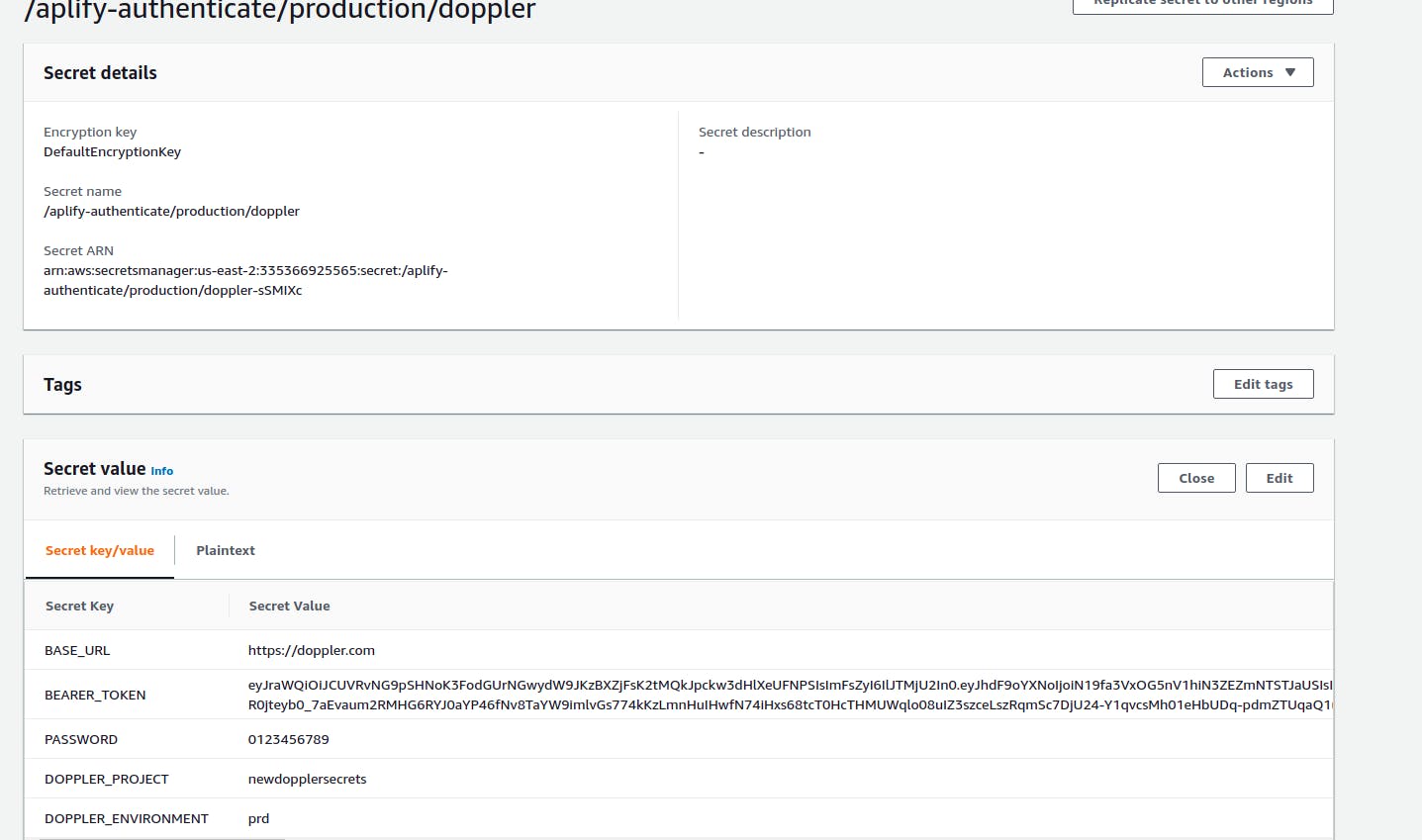
Hurray, we just saved our secrets on Doppler and successfully pushed it to AWS where we can access it for use and whenever we update the secrets on Doppler, it gets updated on AWS automatically.
Conclusion
We have come to the end of this tutorial. We looked at how to use AWS Cognito to create users using their hosted UI. We also learned how to create a lambda function and integrate the lambda function with an API gateway that helped us give JWT tokens to the users and we looked at how to store that token in Doppler.

